hacxx
Uzman Üye
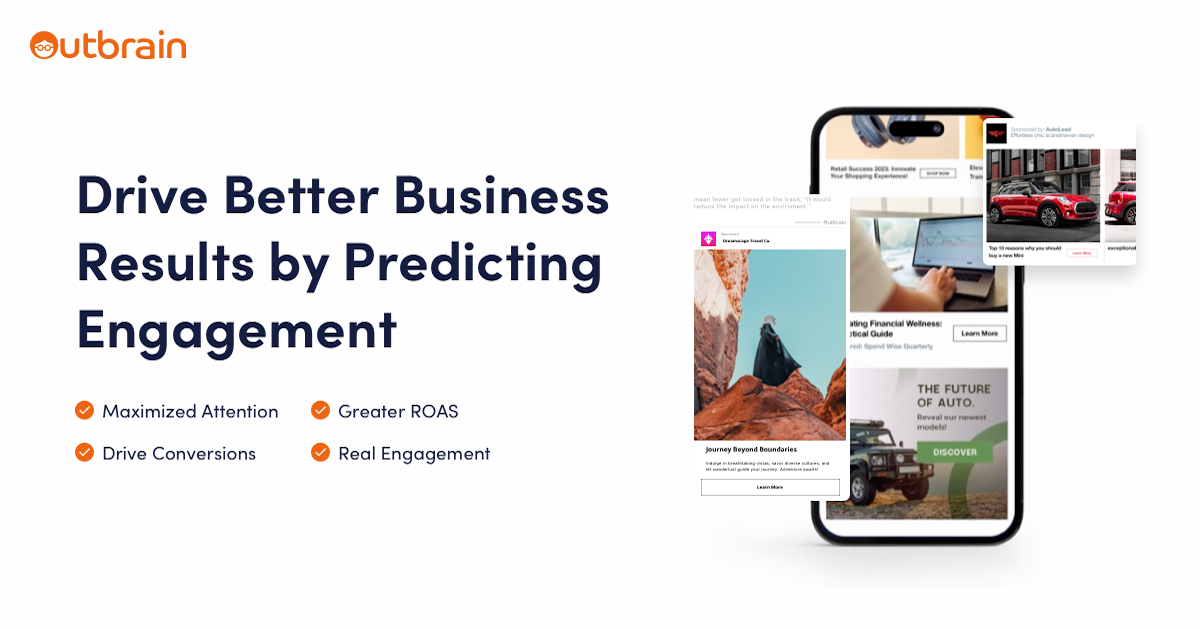
This is a list of Bug Bounty programs and where to get more information to make a responsible disclosure and make profit.

 about.pinterest.com
about.pinterest.com

 activeprospect.com
activeprospect.com
 amara.org
amara.org

 automattic.com
automattic.com

 aws.amazon.com
aws.amazon.com


 cpanel.net
cpanel.net
 en.altervista.org
en.altervista.org
 ethnohub.com
ethnohub.com

 get.harmonyapp.com
get.harmonyapp.com
 help.getpocket.com
help.getpocket.com

 internetbugbounty.org
internetbugbounty.org
 jruby.org
jruby.org
 keepass.info
keepass.info

 mailchimp.com
mailchimp.com

 media.fcanorthamerica.com
media.fcanorthamerica.com
 observu.com
observu.com
 opentext.com
opentext.com
 pages.ebay.com
pages.ebay.com
 scn.sap.com
scn.sap.com

 sproutsocial.com
sproutsocial.com
 support.beanstalkapp.com
support.beanstalkapp.com
 support.iconfinder.com
support.iconfinder.com
 webconverger.org
webconverger.org
 weifund.io
weifund.io

 www-03.ibm.com
www-03.ibm.com
 www.123contactform.com
www.123contactform.com

 www.activecampaign.com
www.activecampaign.com

 www.adapcare.nl
www.adapcare.nl
 www.alcyon.nl
www.alcyon.nl

 www.cisco.com
www.cisco.com

 www.eclipse.org
www.eclipse.org

 www.fluxiom.com
www.fluxiom.com

 www.fogcreek.com
www.fogcreek.com

 www.freelancer.com
www.freelancer.com

 www.gimp.org
www.gimp.org

 www.google.com
www.google.com

 www.google.com
www.google.com
 www.hex-rays.com
www.hex-rays.com


 www.huawei.com
www.huawei.com
 www.infopluscommerce.com
www.infopluscommerce.com
 www.marktplaats.nl
www.marktplaats.nl
 www.mediawiki.org
www.mediawiki.org

 www.meraki.com
www.meraki.com



 www.paychoice.com.au
www.paychoice.com.au

 www.pinoyhacknews.com
www.pinoyhacknews.com
 www.rackspace.com
www.rackspace.com

 www.rijksoverheid.nl
www.rijksoverheid.nl

 www.riotgames.com
www.riotgames.com

 www.rust-lang.org
www.rust-lang.org
 www.skuidify.com
www.skuidify.com
 www.snsbank.nl
www.snsbank.nl
 www.sonatype.com
www.sonatype.com


 www.telecomitalia.com
www.telecomitalia.com

 zetetic.net
zetetic.net


 access.redhat.com
access.redhat.com

 aircloak.com
aircloak.com

 ancientbrain.com
ancientbrain.com

 artifex.com
artifex.com

 asana.com
asana.com

 auth0.com
auth0.com

 badoo.com
badoo.com

 basecamp.com
basecamp.com

 beamery.com
beamery.com

 bitaccess.ca
bitaccess.ca

 bitbns.com
bitbns.com



 blog.airswap.io
blog.airswap.io




 blog.bitwarden.com
blog.bitwarden.com

 blog.centrify.com
blog.centrify.com
 blog.chronobank.io
blog.chronobank.io

 blog.cosmos.network
blog.cosmos.network

 blog.ethfinex.com
blog.ethfinex.com

 blog.genesis.vision
blog.genesis.vision

 blog.gnosis.pm
blog.gnosis.pm

 blog.indorse.io
blog.indorse.io

 blog.iota.org
blog.iota.org

 blog.kyber.network
blog.kyber.network
 blog.leverj.io
blog.leverj.io

 blog.meteor.com
blog.meteor.com

 blog.request.network
blog.request.network

 blog.splitwise.com
blog.splitwise.com

 blog.springrole.com
blog.springrole.com
 blog.vanillaforums.com
blog.vanillaforums.com

 blog.vasco.com
blog.vasco.com
 blog.windingtree.com
blog.windingtree.com
 blogs.technet.microsoft.com
blogs.technet.microsoft.com
 bounty.ethereum.org
bounty.ethereum.org

 bountyfactory.io
bountyfactory.io
 brd.com
brd.com


 bugbounty.linecorp.com
bugbounty.linecorp.com

 bugbounty.prezi.com
bugbounty.prezi.com

 bugcrowd.com
bugcrowd.com

 bugcrowd.com
bugcrowd.com

 bugcrowd.com
bugcrowd.com

 bugcrowd.com
bugcrowd.com

 bugcrowd.com
bugcrowd.com

 bugcrowd.com
bugcrowd.com

 bugcrowd.com
bugcrowd.com

 bugcrowd.com
bugcrowd.com

 bugcrowd.com
bugcrowd.com

 bugcrowd.com
bugcrowd.com

 bugcrowd.com
bugcrowd.com

 bugcrowd.com
bugcrowd.com

 bugcrowd.com
bugcrowd.com
 bugs.php.net
bugs.php.net
 bugzilla.gnome.org
bugzilla.gnome.org

 cappasity.com
cappasity.com
 cayan.com
cayan.com
 chargify.com
chargify.com

 circleci.com
circleci.com

 clickup.com
clickup.com

 clojars.org
clojars.org
 club.hihonor.com
club.hihonor.com

 codeclimate.com
codeclimate.com

 coinspectator.com
coinspectator.com

 connect.teradici.com
connect.teradici.com

 coreos.com
coreos.com
 corporate.tuenti.com
corporate.tuenti.com

 corporate.walmart.com
corporate.walmart.com


 danskebank.com
danskebank.com
 deco.network
deco.network

 detectify.com
detectify.com

 developer.apple.com
developer.apple.com
 discordapp.com
discordapp.com
 dnsimple.com
dnsimple.com

 doc.nuxeo.com
doc.nuxeo.com
 doc.powerdns.com
doc.powerdns.com

 docs.djangoproject.com
docs.djangoproject.com
 docs.joomla.org
docs.joomla.org
 docs.launchkey.com
docs.launchkey.com

 docs.rollbar.com
docs.rollbar.com

 duo.com
duo.com
 en.datocapital.com
en.datocapital.com
 en.internetwache.org
en.internetwache.org

 engineering.quora.com
engineering.quora.com

.png) enterprise.xoxoday.com
enterprise.xoxoday.com
 etherscan.io
etherscan.io
 eventespresso.com
eventespresso.com
 firebounty.com
firebounty.com
 flexlists.com
flexlists.com
 foursquare.com
foursquare.com
 fuga.cloud
fuga.cloud

 gatehub.net
gatehub.net
 gcc.gnu.org
gcc.gnu.org
 getdpd.com
getdpd.com

 github.com
github.com

 glx.co
glx.co

 goo.gl
goo.gl

 groklearning.com
groklearning.com
 hackenproof.com
hackenproof.com




























 help.netflix.com
help.netflix.com
 help.papertrailapp.com
help.papertrailapp.com
 help.ubuntu.com
help.ubuntu.com

 hitbtc.com
hitbtc.com

 honeywell.com
honeywell.com
 hootsuite.com
hootsuite.com
 hunter.io
hunter.io

 ictinstitute.nl
ictinstitute.nl

 instasafe.com
instasafe.com


 keeperchat.com
keeperchat.com

 keepersecurity.com
keepersecurity.com
 kissflow.com
kissflow.com

 kryptocal.com
kryptocal.com
 kuna.io
kuna.io
 localbitcoins.com
localbitcoins.com
 logentries.com
logentries.com

 make.wordpress.org
make.wordpress.org

 managewp.com
managewp.com
 manalyzer.org
manalyzer.org

 matomo.org
matomo.org

 medium.com
medium.com
 medium.com
medium.com

 mytrove.co.nz
mytrove.co.nz

 n26.com
n26.com

 nem.io
nem.io

 nextcloud.com
nextcloud.com

 odn.distilled.net
odn.distilled.net

 openvpn.net
openvpn.net
 orionhealth.com
orionhealth.com

 owncloud.com
owncloud.com
 packetstormsecurity.com
packetstormsecurity.com

 panzura.com
panzura.com

 paritytech.io
paritytech.io
 pentu.eu
pentu.eu
 personal.rbs.co.uk
personal.rbs.co.uk

 polyswarm.io
polyswarm.io

 postmarkapp.com
postmarkapp.com

 proof.work
proof.work

 protonvpn.com
protonvpn.com

 psirt.bosch.com
psirt.bosch.com
 puppet.com
puppet.com
 qwilr.com
qwilr.com

 registry.internetnz.nz
registry.internetnz.nz
 rhinosecuritylabs.com
rhinosecuritylabs.com

 ripple.com
ripple.com
 rocket.chat
rocket.chat
 safehats.com
safehats.com


 secure.sony.net
secure.sony.net


 segment.com
segment.com
 sellfy.com
sellfy.com

 sentry.io
sentry.io

 sifterapp.com
sifterapp.com

 silvergoldbull.ca
silvergoldbull.ca

 silvergoldbull.co.uk
silvergoldbull.co.uk

 slack.com
slack.com
 source.android.com
source.android.com

 squareup.com
squareup.com
 static.draeger.com
static.draeger.com

 success.coupa.com
success.coupa.com
 support.1password.com
support.1password.com

 support.anghami.com
support.anghami.com

 support.bitpay.com
support.bitpay.com

 support.duolingo.com
support.duolingo.com

 support.instamojo.com
support.instamojo.com
 support.kaspersky.com
support.kaspersky.com
 support.lenovo.com
support.lenovo.com

 support.outreach.io
support.outreach.io

 support.phrendly.com
support.phrendly.com

 support.sphero.com
support.sphero.com

 support.upwork.com
support.upwork.com

 tech.showmax.com
tech.showmax.com

 teespring.com
teespring.com


 test.deribit.com
test.deribit.com

 thecargocoin.com
thecargocoin.com

 tls.mbed.org
tls.mbed.org
 torguard.net
torguard.net

 transloadit.com
transloadit.com

 trezor.io
trezor.io
 trustly.com
trustly.com

 typo3.org
typo3.org

 umbraco.com
umbraco.com
 unity3d.com
unity3d.com
 upscope.io
upscope.io
 upscope.io
upscope.io

 vimeo.com
vimeo.com
 vulcoord.cert.org
vulcoord.cert.org

 webuild.envato.com
webuild.envato.com

 werkenbijdefensie.nl
werkenbijdefensie.nl

 wetransfer.com
wetransfer.com

 wickr.com
wickr.com

 www.23andme.com
www.23andme.com

 www.accredible.com
www.accredible.com
 www.actility.com
www.actility.com
 www.aerohive.com
www.aerohive.com

 www.airbnb.com
www.airbnb.com
 www.airmilesshop.nl
www.airmilesshop.nl

 www.algolia.com
www.algolia.com


 www.armis.com
www.armis.com

 www.artsy.net
www.artsy.net


 www.basf.com
www.basf.com

 www.belden.com
www.belden.com

 www.beyondsecurity.com
www.beyondsecurity.com
 www.binary.com
www.binary.com
 www.bitcoin.de
www.bitcoin.de
 www.bitdefender.com
www.bitdefender.com
 www.bitmymoney.com
www.bitmymoney.com


 www.bizmerlin.com
www.bizmerlin.com
 www.blinksale.com
www.blinksale.com

 www.bountysource.com
www.bountysource.com

 www.box.com
www.box.com

 www.bugcrowd.com
www.bugcrowd.com

 www.bugcrowd.com
www.bugcrowd.com

 www.bynder.com
www.bynder.com
 www.campaignmonitor.com
www.campaignmonitor.com
 www.chalk.com
www.chalk.com
 www.chase.com
www.chase.com
 www.cjib.nl
www.cjib.nl

 www.cloudflare.com
www.cloudflare.com
 www.coinjar.com
www.coinjar.com
 www.compose.io
www.compose.io
 www.crowdfense.com
www.crowdfense.com

 www.cylance.com
www.cylance.com
 www.dash.org
www.dash.org

 www.deliveryhero.com
www.deliveryhero.com


 www.dji.com
www.dji.com

 www.docker.com
www.docker.com
 www.doorkeeper.jp
www.doorkeeper.jp

 www.duosecurity.com
www.duosecurity.com

 www.eff.org
www.eff.org

 www.eset.com
www.eset.com

 www.eur.nl
www.eur.nl

 www.expressvpn.com
www.expressvpn.com


 www.facebook.com
www.facebook.com

 www.fastmail.com
www.fastmail.com

 www.firebase.com
www.firebase.com

 www.fireeye.com
www.fireeye.com

 www.first.org
www.first.org

 www.foxy.io
www.foxy.io

 www.freshbooks.com
www.freshbooks.com
 www.gamma.nl
www.gamma.nl
 www.getharvest.com
www.getharvest.com

 www.google.com
www.google.com

 www.google.com
www.google.com

 www.google.com
www.google.com

 www.google.com
www.google.com
 www.gotinder.com
www.gotinder.com
 www.hackerearth.com
www.hackerearth.com

 www.hackerrank.com
www.hackerrank.com

 www.hellosign.com
www.hellosign.com

 www.heroku.com
www.heroku.com
 www.hidglobal.com
www.hidglobal.com

 www.honeycomb.io
www.honeycomb.io

 www.hostinger.com
www.hostinger.com
 www.hyperledger.org
www.hyperledger.org

 www.ifixit.com
www.ifixit.com
 www.ikea.com
www.ikea.com
 www.inflectra.com
www.inflectra.com

 www.ing.com
www.ing.com
 www.intercom.com
www.intercom.com

 www.intigriti.com
www.intigriti.com
 www.intrasurance.com
www.intrasurance.com

 www.ipswitch.com
www.ipswitch.com

 www.jetapps.com
www.jetapps.com


 www.kaseya.com
www.kaseya.com
 www.keepkey.com
www.keepkey.com

 www.ladesk.com
www.ladesk.com

 www.ladesk.com
www.ladesk.com

 www.lahitapiola.fi
www.lahitapiola.fi

 www.lastpass.com
www.lastpass.com

 www.ledger.fr
www.ledger.fr
 www.legalrobot.com
www.legalrobot.com

 www.malwarebytes.org
www.malwarebytes.org

 www.massdrop.com
www.massdrop.com

 www.mattermost.org
www.mattermost.org

 www.maximum.com
www.maximum.com
 www.mimecast.com
www.mimecast.com

 www.mollie.com
www.mollie.com

 www.mozilla.org
www.mozilla.org
 www.ndix.de
www.ndix.de

 www.netgear.com
www.netgear.com
 www.nmbrs.com
www.nmbrs.com

 www.nortonlifelock.com
www.nortonlifelock.com
 www.oath.com
www.oath.com
 www.occrp.org
www.occrp.org

 www.odoo.com
www.odoo.com

 www.offensive-security.com
www.offensive-security.com
 www.olark.com
www.olark.com

 www.openssl.org
www.openssl.org
 www.opera.com
www.opera.com

 www.orange.com
www.orange.com

 www.ovh.co.uk
www.ovh.co.uk

 www.pagerduty.com
www.pagerduty.com


 www.paysera.com
www.paysera.com

 www.philips.com
www.philips.com
 www.polipayments.com
www.polipayments.com

 www.portofrotterdam.com
www.portofrotterdam.com

 www.privateinternetaccess.com
www.privateinternetaccess.com

 www.pushwoosh.com
www.pushwoosh.com
 www.qemu.org
www.qemu.org


 www.qualcomm.com
www.qualcomm.com
 www.rainforestqa.com
www.rainforestqa.com


 www.razer.com
www.razer.com
 www.rcesecurity.com
www.rcesecurity.com
 www.rechtspraak.nl
www.rechtspraak.nl

 www.securepay.com.au
www.securepay.com.au
 www.secureworks.co.uk
www.secureworks.co.uk

 www.sharelatex.com
www.sharelatex.com

 www.shopify.in
www.shopify.in

 www.silentcircle.com
www.silentcircle.com
 www.simpplr.com
www.simpplr.com

 www.siteground.com
www.siteground.com

 www.sli.do
www.sli.do
 www.smokescreen.io
www.smokescreen.io
 www.solaraccounts.co.uk
www.solaraccounts.co.uk

 www.solvinity.com
www.solvinity.com

 www.sophos.com
www.sophos.com

 www.spokeo.com
www.spokeo.com
 www.spotcap.co.nz
www.spotcap.co.nz


 www.spreaker.com
www.spreaker.com

 www.sqreen.io
www.sqreen.io


 www.starleaf.com
www.starleaf.com

 www.stellar.org
www.stellar.org
 www.swisscom.ch
www.swisscom.ch


 www.synology.com
www.synology.com
 www.synopsys.com
www.synopsys.com

 www.talentlms.com
www.talentlms.com

 www.telekom.com
www.telekom.com

 www.tesla.com
www.tesla.com

 www.testbirds.com
www.testbirds.com

 www.theatlantic.com
www.theatlantic.com


 www.trustpay.eu
www.trustpay.eu

 www.uber.com
www.uber.com

 www.ubnt.com
www.ubnt.com

 www.unitag.io
www.unitag.io
 www.vanlanschot.nl
www.vanlanschot.nl
 www.viewpost.com
www.viewpost.com

 www.vodafone.de
www.vodafone.de
 vu.nl
vu.nl
 www.whatruns.com
www.whatruns.com

 www.zynga.com
www.zynga.com

 zapier.com
zapier.com
 zcoin.io
zcoin.io
 zenmate.com
zenmate.com

Responsible disclosure statement

Security Overview - ActiveProspect
Learn how we have achieved SOC 2 Type II compliance and discover which measures we've taken to ensure the security of your business data.
Amara - Caption, translate, subtitle and transcribe video.
The easiest way to caption and translate any video, with crowdsourcing, volunteers, and professional services.

Security
If you have a problem with your password, please contact support. If you have a complaint about a site hosted on WordPress.com, please see our complaints page. If your site has been suspended for a…
 automattic.com
automattic.com

Vulnerability Reporting - Amazon Web Services (AWS)
Report any vulnerabilities you find here.
Earn CPEs with Bug Bounty
Since 2013, (ISC)² has been a partner of Bugcrowd, running a public bug bounty program and offering CPE credits to our members. Bugcrowd is a leading provider of crowdsourced security and bug bounty programs, connecting organizations with more than 50,000 independent security researchers to...
blog.isc2.org

Web Security Tools
campaigns.websecurify.com
Mamba Bug Bounty Program
Mamba pays a reward for every vulnerability found in our apps which was confirmed by our specialists.
corp.wamba.com
cPanel Security Bounty Program | cPanel
In order to show its appreciation for security researchers who follow responsible disclosure principles, cPanel, Inc. is offering a monetary reward program for researchers who provide assistance with identifying and correcting certain Qualifying Vulnerabilities within the scope of this program...
Thanks - Altervista
EthnoHub | Security

Security Overview | Evernote
Our note taking app helps you capture and prioritize ideas, projects and to-do lists, so nothing falls through the cracks. Start your free trial today!
evernote.com
Security - Harmony Website Management
Pocket Help

The Internet Bug Bounty
Security — JRuby.org
Acknowledgements / Credits - KeePass
Keming Labs Security Disclosure
keminglabs.com

Datensicherheit und -schutz bei Mailchimp | Mailchimp
Informationen zur Datensicherheit und zum Datenschutz bei Mailchimp. Mailchimp nimmt Datensicherheit und Datenschutz sehr ernst und wir wissen, dass unsere ...
Stellantis Media - FCA US Launches Bug Bounty Program to Advance Vehicle Cybersecurity
Reflecting the rapidly increasing convergence of connectivity technology and the automotive industry, FCA US LLC today announced the launch of a public bug bounty program on the Bugcrowd platform to enhance the safety and security of its consumers, their vehicles and connected services.
 media.fcanorthamerica.com
media.fcanorthamerica.com
Observu Security
Security Acknowledgements | OpenText
OpenText reviews all reports of security vulnerabilities affecting OpenText products and services.
eBay Security Center
perlsec - Perl security - Perldoc Browser
perldoc.perl.org
Content Unavailable

Responsible Disclosure Policy | Sprout Social
Learn more about the responsible disclosure policy SproutSocial.com, a social media management tool for business.
Responsible Disclosure Policy - Beanstalk Help
Keeping customer data safe and secure is our top priority. If you've discovered a security vulnerability, please do not share it publicly. Instead, report it to
How to report a bug to Iconfinder? | Iconfinder Knowledgebase
Webconverger has better out of the box security
WeiFund - Decentralized Fundraising

IBM PSIRT | IBM Trust Center
Learn how IBM's Security Vulnerability Management program comprehensively addresses security vulnerabilities in IBM products, offerings, and websites.
Security Acknowledgements
Security Acknowledgements We encourage people who find security issues on our platform to immediately report them to our Customer Care Team.

Data Protection and Security | ActiveCampaign
ActiveCampaign is heavily focused on GDPR and HIPAA compliance. Learn more about our approach to data protection and security.

Niet gevonden | Adapcare: ECD voor de care
Alcyon :: Responsible Disclosure

Cisco Security Vulnerability Policy
Debian bug tracking system
www.debian.org
Report A Bug - DNN Open Source Platform | DNN (DotNetNuke)
Report a bug about the latest version of DNN (formerly DotNetNuke) open source CMS and online community software.
www.dnnsoftware.com

Security | The Eclipse Foundation
Security initiatives to ensure the integrity and reliability of the software our community creates and relies on.
Cost of Living Comparisons, 2025 data.
Cost of Living comparisons for thousands of cities. Fully up-to-date cost of living comparisons, including prices of 52 products and services.
www.expatistan.com

Fluxiom - Simplify Your Digital Asset Management Experience
Reporting a security issue to Fluxiom Fluxiom engineers continuously monitor our network for indications of security vulnerabilities that may put customer data at risk. Should ...

Glitch: The friendly community where everyone builds the web
Simple, powerful, free tools to create and use millions of apps.

Security Reporting | Freelancer
Tell Freelancer about security vulnerabilities in their website and be recognised for your contributions.

GIMP - Bugs
If you think you found a bug, it is very important to report it. If the developers don’t know about what might be broken, they can’t fix it. So there you are at your computer trying to do something with GIMP and it freaks out at you. It …

Google and Alphabet Vulnerability Reward Program (VRP) Rules | Google Bug Hunters
We have long enjoyed a close relationship with the security research community. To honor all the cutting-edge external contributions that help us keep our users safe, we maintain a Vulnerability Reward Program for Google-owned and Alphabet (Bet)...

Google and Alphabet Vulnerability Reward Program (VRP) Rules | Google Bug Hunters
We have long enjoyed a close relationship with the security research community. To honor all the cutting-edge external contributions that help us keep our users safe, we maintain a Vulnerability Reward Program for Google-owned and Alphabet (Bet)...
Hex-Rays Security Bug Bounty Program

Reporting Suspected Vulnerabilities
InfoPlus | Legal Documents
Your privacy is important to us at InfoPlus. We want to be clear how we use your information and the ways in which you can protect your privacy.
IntegraXor HMI/SCADA Bug Bounty Program - Ecava IGX Web SCADA
IntegraXor HMI/SCADA Bug Bounty Program This Non-Monetary Bug Bounty Program is part of our effort to make IntegraXor SCADA more secure, safe & stable. Below are the rules for joining. Terms & conditions apply. Considerations We only concern on the issue that will impact our customers’...
www.integraxor.com
Maddysoft
www.maddysoft.com
Marktplaats - Help & Info
How to report a bug - MediaWiki

Trust


Data Management Solutions for the Cloud | NetApp
Modernize your data management systems and simplify cloud data storage with NetApp – the world’s leader in data management solutions.
www.netapp.com
OpenBSD: Security
www.openbsd.org

PayChoice | Online Payment Solutions | Payments Australia
Streamline your payment processing with PayChoice, the online payment solution for over 3000 Australian businesses.

Responsible Disclosure - Pinoy Hack News - PHN
I am glad to announce that we are embracing a bug bounty program. In the moment, since we are just a small company we can only list you in our Hall of Fame as a token of appreciation- Responsible Disclosure
Rackspace Technology Security Vulnerability Reporting

Kwetsbaarheid melden
Ontdekt u een zwakke plek of kwetsbaarheid op deze website, meld dit dan aan het Nationaal Cyber Security Centrum (NCSC). Het maken van zo'n melding heet Coordinated Vulnerability Disclosure (CVD).
Security

Security policy
A language empowering everyone to build reliable and efficient software.
Skuid security overview
Veilig bankieren
We werken elke dag hard om te zorgen dat je je bankzaken veilig kunt regelen bij SNS.
Contact Us Your Software Supply Chain Experts
Get in touch with our experts today to help secure your software supply chain. Get product support, become a partner, or connect about media inquiries.


Responsible Disclosure

Redirecting...
www.twitch.tv
Secure Contact and Security Disclosures | Zetetic
Public key contact information for Zetetic


Vulnerability Acknowledgements for Red Hat online services - Red Hat Customer Portal
Vulnerability Acknowledgements for Red Hat online services.

Attack Challenge | Aircloak
Mehr Transparenz und Sicherheit: Die Aircloak Attack Challenge ist das weltweit erste Bounty-Programm für eine Anonymisierungsmethode.

Bug bounty [Ancient Brain]

Bug Bounty Program | Artifex
Information related to the Ghostscript and MuPDF Bug Bounty Program.

Asana | Bugcrowd
Learn more about Asana’s Bug Bounty engagement powered by Bugcrowd, the leader in crowdsourced security solutions.

Auth0 by Okta | Bugcrowd
Learn more about Okta’s Bug Bounty engagement powered by Bugcrowd, the leader in crowdsourced security solutions.

Bumble Tech – Medium
We’re the tech team behind social networking apps Bumble and Badoo. Our products help millions of people build meaningful connections around the world.
 badoo.com
badoo.com

Security Response
Have you discovered a web security flaw that might impact one of our products? Here’s how you can report it.

Security | Beamery
Explore how Beamery ensures privacy and security data at all levels: in our work, across our organization, and in our platform.

Introducing Our Bug Bounty Program - Bitaccess
Today, we’re happy to announce the opening of our bug bounty program to the developer community. Bitaccess has long maintained private bounty programs, allowing security researchers to analyze pre- and […]
 bitaccess.ca
bitaccess.ca

Bitbns Bug Bounty Program
Bitbns Invites individuals and companies to test and report errors if found.
 bitbns.com
bitbns.com


Smart Contracts and Bug Bounty
Update Dec 3, 2019: This article is out of date. See the latest Bug Bounty.
 blog.airswap.io
blog.airswap.io




The Bitwarden Blog
Blogs, news, updates, and information of all kinds can be found here at the Bitwarden Blog.

Centrify's Bug Bounty Program with Bugcrowd | Centrify
That’s why I am very happy to announce that Centrify has opened a public bug bounty program today with the help of Bugcrowd.

ChronoWallet Bug Bounty
We believe in a Bug Bounty program that fosters collaboration amongst professionals to help us building the most secure and useful wallet…
 blog.chronobank.io
blog.chronobank.io

Bug Bounty Program for Tendermint & Cosmos
At Tendermint, we believe that security researchers and white hat hackers are a vital part of building strong, resilient cryptocurrency…
 blog.cosmos.network
blog.cosmos.network

Nectar Token Bug Bounty | rhino.fi
As we approach the launch of Ethfinex and the Nectar token, we are now running an open bug bounty program for the Ethereum community to analyse our token co ...

Genesis Vision Bounty Program
We believe in a decentralized economy and cryptocurrency community. The Bounty program is aimed at engaging community in our campaign…
 blog.genesis.vision
blog.genesis.vision

DutchX and Initial OWL Generation Bug Bounty
We’re excited to announce that we are conducting a bug bounty for all contracts relevant for our upcoming DutchX release as well as the…
 blog.gnosis.pm
blog.gnosis.pm

Indorse Bug Bounty Program
Today, we are publishing a Smart Contract for public review.

Bug Bounty: Current List of Payouts
The IOTA Bug Bounty program was announced now more than a month ago. During this timeframe many of the existing, but also new community members participated in the bug hunting. In total, we have found more than 35 issues (mostly in the low category) which the dev team quickly resolved.
 blog.iota.org
blog.iota.org

Kyber Network Exchange Bug Bounty
Updates: This bug bounty was created for the first mainnet deployment. We are still running on-going bug bounty campaigns for various code…
 blog.kyber.network
blog.kyber.network

Announcing the 1 Million LEV Bug Bounty
The Leverj staking contract is running on ropsten and very soon will be running on mainnet.
 blog.leverj.io
blog.leverj.io

Meteor allow/deny vulnerability disclosure
A security bug in a common Meteor configuration which requires your attention
 blog.meteor.com
blog.meteor.com

Request Network Foundation
Request Network provides Web3 infrastructure for invoicing, payments, accounting, and more.
 blog.request.network
blog.request.network
Responsible Disclosure / Special Thanks
At Splitwise, we’re lucky to have supportive users who help us to find bugs and potential security vulnerabilities via responsible disclosure. If you believe you have discovered a potential issue w…

Springworks Blog
We want to help you learn about the human resources and employee engagement. Get practical advice on remote work, team building, and succeeding at work.
Blog | Higher Logic
Check out Logic's blog for increasing association member engagement, improving your online community and keeping your customers happy. Read articles from our blog now!

Blog

Lif TGE Bug Bounty Program
We’re excited to announce that we are starting our bug bounty ahead of the Líf Token Generation Event. We believe bug bounties are…
 blog.windingtree.com
blog.windingtree.com

Announcing the Windows Bounty Program – Microsoft Security Response Center

Ethereum Bug Bounty Program
An overview of the Ethereum bug bounty program: how to get involved and reward information.

YesWeHack - Global Bug Bounty & Vulnerability Management Platform
YesWeHack is a global Bug Bounty & Vulnerability Management Platform. With a worldwide presence, YesWeHack connects organisations to tens of thousands of bug hunters. The aim is to uncover and patch vulnerabilities in websites, mobile apps, connected devices and digital infrastructure.
 bountyfactory.io
bountyfactory.io
A Cryptocurrency Wallet | BRD
BRD is the simple and secure way to get started with Bitcoin, Ethereum and other cryptocurrencies.

Zendesk Sell Bug Bounty Program
bugbounty.getbase.com

LINE Security Bug Bounty Program
LY Corporation will host the LINE Security Bug Bounty Program.

Prezi
Prezi designs and creates presentation software that is enabling millions of people to be great presenters.

Appliances - Barracuda Networks, Inc. | Bugcrowd
Learn more about Barracuda Networks’s Bug Bounty engagement powered by Bugcrowd, the leader in crowdsourced security solutions.

Cisco Meraki | Bugcrowd
Learn more about Meraki’s Bug Bounty engagement powered by Bugcrowd, the leader in crowdsourced security solutions.

Constant Contact, Inc. | Bugcrowd
Learn more about Constant Contact ’s Vulnerability Disclosure engagement powered by Bugcrowd, the leader in crowdsourced security solutions.

eero’s vulnerability disclosure program | Bugcrowd
Learn more about eero’s vulnerability disclosure program powered by Bugcrowd, the leader in crowdsourced security solutions.

Fitbit’s bug bounty program | Bugcrowd
Learn more about Fitbit’s bug bounty program powered by Bugcrowd, the leader in crowdsourced security solutions.

SecureDrop | Bugcrowd
Learn more about Freedom of the Press Foundation’s Bug Bounty engagement powered by Bugcrowd, the leader in crowdsourced security solutions.

Humble Bundle | Bugcrowd
Learn more about Humble Bundle’s Bug Bounty engagement powered by Bugcrowd, the leader in crowdsourced security solutions.

Indeed | Bugcrowd
Learn more about Indeed’s Bug Bounty engagement powered by Bugcrowd, the leader in crowdsourced security solutions.

Intercom | Bugcrowd
Learn more about Intercom’s Bug Bounty engagement powered by Bugcrowd, the leader in crowdsourced security solutions.

Beyond, Inc. | Vulnerability Disclosure Program | Bugcrowd
Learn more about Overstock.com’s Vulnerability Disclosure engagement powered by Bugcrowd, the leader in crowdsourced security solutions.

Socrata’s bug bounty program | Bugcrowd
Learn more about Socrata’s bug bounty program powered by Bugcrowd, the leader in crowdsourced security solutions.

Statuspage | Bugcrowd
Learn more about Atlassian’s Bug Bounty engagement powered by Bugcrowd, the leader in crowdsourced security solutions.

Western Union | Bugcrowd
Learn more about Western Union’s Bug Bounty engagement powered by Bugcrowd, the leader in crowdsourced security solutions.
Site moved!
bugs.archlinux.org
PHP :: Report - New
GNOME Bugzilla

Cappasity is the platform for production of immersive shopping experiences
Cappasity is a cloud-based platform that lets online stores easily create and deliver 3D, AR and NFT shopping experiences. 3D and 360 Product Photography.
Semi-Integrated Solutions for Merchants
Our semi-integrated unified commerce solution connects every channel, so merchants can engage their customers while shopping online and in-store.
Secure billing software
PCI compliant, secure billing software to protect you and your customers. Proven reliability to keep your recurring billing running smoothly.

Your security is our priority
From encryption to audit logs and top-tier security certifications, learn what CircleCI is doing to keep your data safe.
 circleci.com
circleci.com

ClickUp™ | Security & Bug Reporting Program
Please email us at [email protected] with any vulnerability reports or questions about the program. We'll make it worth your while.

Security
HONOR CLUB (Global)
HONOR CLUB (Global) offers rich and high-quality content around its various products, including smartphones, wearables, laptops and accessories. Also, you are welcome to participate in exciting activities online.

Security
Code Climate is trusted by thousands of organizations to deliver the power of cloud-scale machine learning without risk to your code.
Cryptocurrency News - CoinSpectator
CoinSpectator. Real-time cryptocurrency news aggregator for traders, investors and enthusiasts. Est 2013. Advertise with us or submit news article. Bitcoin
 coinspectator.com
coinspectator.com

Bug Reporting - EVE Community
Eve Online is the world's largest MMO RPG universe rich in adventure, as player corporations compete in a massively multiplayer online space game.
community.eveonline.com
Report A Vulnerability
If you have found a security vulnerability on Teradici products, please let us know.

Security contacts and procedures - Red Hat Customer Portal
Instructions for contacting Red Hat Product Security
Tuenti: la compañía móvil que te ofrece mucho más
Tuenti tiene una oferta inigualable que ninguna otra compañía puede ofrecerte: llamadas, gigas, la mejor cobertura, chat y llamadas sin límites con la app, y mucho más.
Responsible Disclosure Policy
If you are a security researcher and have discovered a security vulnerability in one of our services or sites, we encourage you to disclose it to us in a responsible manner.


Responsible Disclosure
Contact us, if you discover any vulnerabilities on our websites and help us improve the safety and reliability of our systems.
Deconet Bounty Program

Responsible Disclosure
We take security issues seriously & respond swiftly to fix verifiable security issues. Report yours to [email protected]. Keep the internet secure!

Bug Reporting - Apple Developer
Now with Feedback Assistant available on iPhone, iPad, Mac, and the web, it’s easier to submit effective bug reports and request enhancements to APIs and tools.

Security Bug Bounty | Discord
As part of our commitment to security, we reward security researchers for reporting security vulnerabilities responsibly to us.
DNSimple Security - DNSimple
DNSimple helps you safeguard your domains with DDoS Defense combined with other security features like multi-factor authentication and activity logging.

How to Submit a Bug Report
How to Submit a Bug Report. Learn how to get started with Nuxeo documentation.
Security of PowerDNS — PowerDNS Authoritative Server documentation

Archive of security issues | Django documentation
The web framework for perfectionists with deadlines.
How do you report a bug? - Joomla! Documentation
White Hat Program - TruValidate Multifactor Authentication Documentation
TruValidate Multifactor Authentication documentation

Responsible Disclosure Policy
Rollbar aims to keep its Services safe for everyone, and data security is of utmost priority. If you are a security researcher and have discovered a security vulnerability in the Services, we appreciate your help in disclosing it to us in a responsible manner. Rollbar will engage with security...
 docs.rollbar.com
docs.rollbar.com
Drupal Security Team
Goals of the security team Resolve reported security issues in a Security Advisory Provide assistance for contributed module maintainers in resolving security issues Provide documentation on how to write secure code Provide documentation on securing your site Help the infrastructure team to keep...
drupal.org

Duo Security Disclosure & Bug Handling Policy
Learn how Duo Labs handles vulnerability disclosure as well as what security researchers and customers can expect when they disclose a vulnerability to Duo.
Report Security Issue
As a worldwide provider of business and financial information, security is one of our top priorities. We process millions of company and director...
Responsible Disclosure - Internetwache - A secure internet is our concern
Responsible Disclosure Security isn’t easy, and we all know it. That’s why we’re running a responsible disclosure program. …

Engineering at Quora

First 100 Days of Yelp's Public Bug Bounty Program
First 100 Days of Yelp's Public Bug Bounty Program Martin Georgiev, Software Engineer Dec 20, 2016 One hundred days ago we launched Yelp’s public bug bounty program on HackerOne. Since...
engineeringblog.yelp.com
Xoxoday Home
Bot Challenge
esp32.com
Etherscan Bug Bounty Page
Event Espresso
FireBounty | The Ultimate Vulnerability Disclosure Policy and Bug Bounty List!
FireBounty, aggregate your bounty
FlexLists - About
Use FlexLists to create sharable lists of tasks, issues, literature and more.
Security
Responsible Disclosure Policy - Fuga Cloud
As a hosting provider, we consider the security of our systems and those of our customers highly important. If you have found a weak spot we would like to hear from you.

GateHub Wallet
GateHub is a platform for the Internet of Value. Built on XRP Ledger protocol it allows everyone to send, receive, trade and manage any type of assets.
GCC Bugs - GNU Project
DPD - Security Disclosures
DPD encourages the responsible disclosure of security vulnerabilities
GitHub - sass/libsass: A C/C++ implementation of a Sass compiler
A C/C++ implementation of a Sass compiler. Contribute to sass/libsass development by creating an account on GitHub.

GLX.com - Capital Market Directory & Social Finance Network
GLX.com is a Capital Market Directory and Social Finance Network. The destination is a global capital market news data portal and ground-breaking financial networking platform.

Report | Google Bug Hunters
Found a security vulnerability? Discover our forms for reporting security issues to Google: for the standard VRP, Google Play, and Play Data Abuse.

Grok Academy
We want to make Grok Academy a safe and secure learning environment for all. If you've discovered a vulnerability in Grok Academy, we appreciate your help in disclosing it in a responsible manner.
HackenProof | Web3 Bug Bounty platform for Crypto Projects
HackenProof is a leading bug bounty platform in the web3 space. HackenProof’s primary aim is to offer crowdsourced services such as bug bounty programs, smart contract contests

Bime - Bug Bounty Program | HackerOne
The Bime Bug Bounty Program enlists the help of the hacker community at HackerOne to make Bime more secure. HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited.
hackerone.com
Blockchain - Bug Bounty Program | HackerOne
The Blockchain Bug Bounty Program enlists the help of the hacker community at HackerOne to make Blockchain more secure. HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited.
hackerone.com

Booking.com - Bug Bounty Program | HackerOne
The Booking.com Bug Bounty Program enlists the help of the hacker community at HackerOne to make Booking.com more secure. HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited.
hackerone.com

C2FO - Vulnerability Disclosure Program | HackerOne
The C2FO Vulnerability Disclosure Program enlists the help of the hacker community at HackerOne to make C2FO more secure. HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited.
hackerone.com

HackerOne
This community-curated security page documents any known process for reporting a security vulnerability to Cobalt, often referred to as vulnerability disclosure (ISO 29147), a responsible disclosure policy, or bug bounty program.
hackerone.com
Coinbase - Bug Bounty Program | HackerOne
The Coinbase Bug Bounty Program enlists the help of the hacker community at HackerOne to make Coinbase more secure. HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited.
hackerone.com

Deconf - Vulnerability Disclosure Program | HackerOne
The Deconf Vulnerability Disclosure Program enlists the help of the hacker community at HackerOne to make Deconf more secure. HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited.
hackerone.com

Deliveroo - Bug Bounty Program | HackerOne
The Deliveroo Bug Bounty Program enlists the help of the hacker community at HackerOne to make Deliveroo more secure. HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited.
hackerone.com

U.S. Dept Of Defense - Vulnerability Disclosure Program | HackerOne
The U.S. Dept Of Defense Vulnerability Disclosure Program enlists the help of the hacker community at HackerOne to make U.S. Dept Of Defense more secure. HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be...
hackerone.com
Dyson - Bug Bounty Program | HackerOne
The Dyson Bug Bounty Program enlists the help of the hacker community at HackerOne to make Dyson more secure. HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited.
hackerone.com

ExpressionEngine - Vulnerability Disclosure Program | HackerOne
The ExpressionEngine Vulnerability Disclosure Program enlists the help of the hacker community at HackerOne to make ExpressionEngine more secure. HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited.
hackerone.com

GlassWire - Bug Bounty Program | HackerOne
The GlassWire Bug Bounty Program enlists the help of the hacker community at HackerOne to make GlassWire more secure. HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited.
hackerone.com
Greenhouse.io - Bug Bounty Program | HackerOne
The Greenhouse.io Bug Bounty Program enlists the help of the hacker community at HackerOne to make Greenhouse.io more secure. HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited.
hackerone.com
HackerOne
This community-curated security page documents any known process for reporting a security vulnerability to Helpscout, often referred to as vulnerability disclosure (ISO 29147), a responsible disclosure policy, or bug bounty program.
hackerone.com
HackerOne
This community-curated security page documents any known process for reporting a security vulnerability to Hybrid Saas, often referred to as vulnerability disclosure (ISO 29147), a responsible disclosure policy, or bug bounty program.
hackerone.com
Instacart - Bug Bounty Program | HackerOne
The Instacart Bug Bounty Program enlists the help of the hacker community at HackerOne to make Instacart more secure. HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited.
hackerone.com

LeaseWeb - Bug Bounty Program | HackerOne
The LeaseWeb Bug Bounty Program enlists the help of the hacker community at HackerOne to make LeaseWeb more secure. HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited.
hackerone.com

LinkedIn - Bug Bounty Program | HackerOne
The LinkedIn Bug Bounty Program enlists the help of the hacker community at HackerOne to make LinkedIn more secure. HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited.
hackerone.com

HackerOne
This security page documents any known process for reporting a security vulnerability to McAfee, often referred to as vulnerability disclosure (ISO 29147), a responsible disclosure policy, or bug bounty program.
hackerone.com
HackerOne
This community-curated security page documents any known process for reporting a security vulnerability to Massachusetts Institute of Technology, often referred to as vulnerability disclosure (ISO 29147), a responsible disclosure policy, or bug bounty program.
hackerone.com

Mobile Vikings - Vulnerability Disclosure Program | HackerOne
The Mobile Vikings Vulnerability Disclosure Program enlists the help of the hacker community at HackerOne to make Mobile Vikings more secure. HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited.
hackerone.com

Nearby Live - Bug Bounty Program | HackerOne
The Nearby Live Bug Bounty Program enlists the help of the hacker community at HackerOne to make Nearby Live more secure. HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited.
hackerone.com
HackerOne
This security page documents any known process for reporting a security vulnerability to Nest, often referred to as vulnerability disclosure (ISO 29147), a responsible disclosure policy, or bug bounty program.
hackerone.com
Nimiq - Bug Bounty Program | HackerOne
The Nimiq Bug Bounty Program enlists the help of the hacker community at HackerOne to make Nimiq more secure. HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited.
hackerone.com
Paragon Initiative Enterprises - Bug Bounty Program | HackerOne
The Paragon Initiative Enterprises Bug Bounty Program enlists the help of the hacker community at HackerOne to make Paragon Initiative Enterprises more secure. HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be...
hackerone.com
HackerOne
This community-curated security page documents any known process for reporting a security vulnerability to ReleaseWire, often referred to as vulnerability disclosure (ISO 29147), a responsible disclosure policy, or bug bounty program.
hackerone.com

HackerOne - Bug Bounty Program | HackerOne
The HackerOne Bug Bounty Program enlists the help of the hacker community at HackerOne to make HackerOne more secure. HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited.
hackerone.com

StopTheHacker - Vulnerability Disclosure Program | HackerOne
The StopTheHacker Vulnerability Disclosure Program enlists the help of the hacker community at HackerOne to make StopTheHacker more secure. HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited.
hackerone.com
X / xAI - Bug Bounty Program | HackerOne
The X / xAI Bug Bounty Program enlists the help of the hacker community at HackerOne to make X / xAI more secure. HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited.
hackerone.com
VK.com - Vulnerability Disclosure Program | HackerOne
The VK.com Vulnerability Disclosure Program enlists the help of the hacker community at HackerOne to make VK.com more secure. HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited.
hackerone.com
Yahoo! - Bug Bounty Program | HackerOne
The Yahoo! Bug Bounty Program enlists the help of the hacker community at HackerOne to make Yahoo! more secure. HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited.
hackerone.com
Responsible Vulnerability Disclosure
How security researchers can report security vulnerabilities via our bug bounty program.
Documentation for Papertrail - Papertrail
Aggregate Logs Configure your apps and services, hosting services, and integrations to send logs to Papertrail. For common configurations, you can find step-by-step instructions directly in Papertrail. Or look at […]
Introduction | Ubuntu
Ubuntu is an open source software operating system that runs from the desktop, to the cloud, to all your internet connected things.

Bug Report / HitBTC
Contact our development team to leave your feedback or submit a bug report.

Product Security
Our goal is to minimize customers’ risk associated with security vulnerabilities by providing timely information, guidance, and more.
Hootsuite - Security Response
Hootsuite - Social Media Management. With Hootsuite, you can monitor keywords, manage multiple Twitter, Facebook, LinkedIn, and Foursquare profiles, schedule messages, and measure your success.

Security Bounty Program • Hunter
The security of our users’ data is a priority. We welcome help from the outside through our bounty program to put our security to the test.

Getting started with a responsible disclosure policy - ICT Institute
A responsible disclosure policy allows people to test the security of your IT. It is a highly recommended security measure for larger organisations: it gives more insight, reduces incidents and helps find security talent. What is responsible disclosure? Many hackers are simply enthusiasts that...
 ictinstitute.nl
ictinstitute.nl

Security at Instasafe | Responsible Disclosure policy
InstaSafe takes security seriously. Join our vulnerability rewards program or report security issues responsibly. Help us keep InstaSafe secure for everyone.


KeeperChat: World's Most Secure Messaging App | Keeper Security
Explore KeeperChat, the world's most secure messaging app available on all devices. Protect your communications and conversations whether business or personal.

Best Password Manager Security & Data Protection | Keeper Security
Learn more about Keeper's zero-knowledge security architecture, encryption methodologies, hosting environment and data protection. Millions of consumers and thousands of businesses trust Keeper as their preferred web password manager. Start your free trial today!
Responsible Disclosure - Kissflow
We take the responsibility seriously. Learn about our commitment to transparency and social responsibility. Explore our disclosure now.
 kissflow.com
kissflow.com

Upcoming Crypto Currency Bounty Campaigns in June - kryptocal.com
KryptoCal is a platform which provides cryptocurrency related events/ICO dates at your fingertips. We have created a variety of ways for you to access these events. You can download our app from Apple
KUNA
LocalBitcoins whitehat program - LocalBitcoins
Security
Our Focus on SecurityYour data security is of paramount importance to us at Logentries. Our focus on security cuts across every layer of the Logentries platform, and the service was designed from the ground up as a secure, highly available, and massively scalable multi-tenant log management and...

Reporting Bugs
Reporting Security Issues While we try to be proactive in preventing security problems, we do not assume they’ll never come up. If you believe you’ve found a security problem in a relea…

White Hat Reward - ManageWP
Every day we do our best to make sure ManageWP is running safely and securely. But we’re only human, and there’s always a chance that we missed something. That’s where our mighty contributors came in – they found a weakness in our security, collected the cash reward and got listed as a contributor!
Manalyzer :: Bug Bounty

Matomo Security Bug Bounty Programme
Take part in the Matomo Security Bug Bounty Programme and play a crucial role by letting us know of crucial security issues you find using Matomo!
Medium: Read and write stories.
On Medium, anyone can share insightful perspectives, useful knowledge, and life wisdom with the world.
Medium’s Bug Bounty Disclosure Program
PLEASE NOTE: As of August, 2023 our bug bounty program is paused. All submitted reports will be address, but we are not accepting new…
 medium.com
medium.com

myTrove

N26 Bug Bounty Program
Are you a Bug Bounty Hunter? Want to improve the security of a mobile bank? Join our HackerOne program and search for vulnerabilities.

Discord | Your Place to Talk and Hang Out
Discord is the easiest way to talk over voice, video, and text. Talk, chat, hang out, and stay close with your friends and communities.


Updates about the Nextcloud Bug Bounty Program - Nextcloud
Nearly one year ago we introduced the Nextcloud bug bounty program offering a significant monetary reward for reports of security vulnerabilities within Nextcloud. Security Bug Bounties are a ‘security best practice’ followed by large organizations like Microsoft, Uber, Github, Twitter and Slack...

Enterprise-Ready Security and Compliance Certification - SearchPilot
PCI compliant, ISO 27001 certified, HIPAA compliant, and regularly penetration-tested to help you have confidence in the platform’s security.

Why OpenVPN Supports OSTIF's Bug Bounty Program | OpenVPN
OpenVPN is supporting OSTIF’s efforts in engaging the brilliant minds in the community to maintain high cyber security standards.
 openvpn.net
openvpn.net
Healthcare Product Documentation | Orion Health
Access Orion Health's comprehensive healthcare documentation (DOKI) for resources and support for all our products and services.

Contribute bright ideas - ownCloud
Contribute to ownCloud we are supported by a passionate community of users and developers from around the world. See how you can join today!
Packet Storm
Information Security Services, News, Files, Tools, Exploits, Advisories, and Whitepapers
How to Report a Bug
panic.com
Home
Modernize storage infrastructure. Make file data bulletproof. Boost productivity & security with hybrid cloud file services & data management.
Announcing the Bug Bounty Program
As recent events have shown us, it's not always enough to have good programmers, open-source software and peer reviews in order to ensure no…
News | Pentu.eu
Security Centre | Fraud and Scams | Royal Bank
Learn how to protect yourself from fraud and scams and see how we're protecting our customers. Visit our Security Centre.

Bug Bounty Programm for Bugs and Critical Security Issues
Bug Bounty Programm for Bugs and Critical Security Issues
plesk.uservoice.com
Security - PolySwarm
PolySwarm is a crowdsourced threat detection marketplace where security experts & AV companies compete to protect you.

Responsible Disclosure Policy | Postmark Support Center
Keeping customer data safe and secure is our top priority.If you’ve discovered a security vulnerability, please do not share it publicly. Instead, report…

Bounty
 proof.work
proof.work

Keeping Proton VPN Secure | Proton VPN
We are launching the Proton VPN Bug Bounty Program. With this program, we are inviting security experts from around the world to try to find weaknesses in Proton VPN.

Bosch PSIRT
The Bosch PSIRT is the central point of contact to report cybersecurity information related to products and websites of Bosch and its brands.
Puppet Security | Puppet
Discover Puppet's security policy and how Puppet addresses security vulnerabilities.
Vulnerability Disclosure Program
Qwilr's vulnerability disclosure program aims to recognise security researchers who responsibly disclose vulnerabilities to us.

Report a vulnerability
This page is the place to report vulnerabilities and security issues with any of our online systems at InternetNZ. Find out more about the process here.
Vulnerability Disclosure Policy
Vulnerabilities discovered by Rhino Security Labs in its research will be disclosed 45 days after the initial report, regardless of patching by the vendor.

Bug Bounty
We offer a bounty for any security-relevant bugs in our software. Learn more about our bug bounty for exploits, vulnerabilities and ongoing attacks.
Page not found - Rocket.Chat Docs
Disclosure Policy - SafeHats | Managed Bug Bounty Program
Disclosure Policy 1. Responsible Disclosure Policy Effective disclosure policy requires mutual trust, respect, and transparency between the security researchers and our security team. We request you to report any bug as soon as you discover. We request you not to do any public disclosure before...
 safehats.com
safehats.com

Help for your Yahoo Account
safety.yahoo.com

Secure@Sony
The Secure@Sony program accepts reports of bugs that provide a potential attacker with the ability to compromise the integrity, availability or confidentiality of Sony products, services or information technology infrastructure and that meet our submission guidelines.

Twilio Terms of Service
With Twilio, unite communications and strengthen customer relationships across your business – from marketing and sales to customer service and operations.
Security
The following researchers have taken the time to identify and report security concerns with Sellfy.

Security & Compliance
Sentry is committed to security and compliance, including protecting your application’s data, eliminating systems vulnerability, and ensuring access continuity.
Security & Responsible Disclosure
SifterApp.com security information and responsbile disclosure policy.

Build your wealth in ounces
We Offer Gold and Silver Coins, Rounds, Wafers and Bars including Silver Maple Leaf and Gold Maple Leaf coins

Bug Bounty | Silver Gold Bull UK
We Offer Gold and Silver Coins, Rounds, Wafers and Bars including Silver Maple Leaf and Gold Maple Leaf coins

Report a Vulnerability | Legal
Report a vulnerability. If you believe you have found a security vulnerability on Slack, please let us know right away so we can investigate promptly. Thank you.
Report and track bugs | Android Open Source Project

Secure Payments Systems - Trusted Payment Solutions - Square
Square’s secure payment system is dedicated to protecting your business from frauds, chargebacks and more. Learn how Square handles payment security.
Dräger Security | Coordinated Disclosure Statement
Dräger Product Security - Coordinated Disclosure Statement. Here's how you can report a security or privacy vulnerability to Dräger.
 static.draeger.com
static.draeger.com

Vulnerability Reporting Policy
We welcome vulnerability reports from independent security researchers via [email protected].

Security audits of 1Password | 1Password Support
1Password products have been reviewed by multiple independent security firms.

Bug Reporting Program
Find a bug, get Anghami Plus! Anghami will gift users who report a serious bug. Rewards can range from a month to months of Anghami Plus depending on the severity of the vulnerability ■ OUR REW...
 support.anghami.com
support.anghami.com

Does BitPay have a bug bounty program?
BitPay values its close relationship with the security research community. To show its appreciation for external contributions, BitPay maintains a Bug Bounty Program designed to reward responsible ...
 support.bitpay.com
support.bitpay.com

How do I report a bug?
If you think that Duolingo is not behaving as expected, we would appreciate it if you'd let us know. We collect bug reports sent by users to detect emergencies and other issues. Please note that bu...

Instamojo Bug Bounty Policy
Eligibility Reporter eligibility You must NOT be an employee of Instamojo within the last 6 months. You must NOT be an immediate family member of an Instamojo employee. You must be a citizen of In...
 support.instamojo.com
support.instamojo.com
Отчет по уязвимостям: Общая информация
Узнайте больше об отчете по уязвимостям от Лаборатории Касперского.
Lenovo Vulnerability Disclosure Policy - Redirect - Lenovo Support US

GDPR Compliance
Purpose: The purpose of this article is to provide information to Outreach Users regarding General Data Protection Regulation (GDPR) compliance. General Data Protection Regulation (GDPR) Complian...
 support.outreach.io
support.outreach.io
Do you have a “bug bounty” if I find an issue with your site?
**If you simply need help with your account, please contact Customer Support via email to [email protected]** At Phrendly, keeping our members' personal information private and secure is a pri...

Vulnerability Disclosure Program
Important Notice Effective January 1, 2020, Sphero's vulnerability disclosure program is closed. Reports submitted prior to January 1, 2020 will be brought to closure. Reports submitted after Decembe…
 support.sphero.com
support.sphero.com

Report Site Vulnerabilities
At Upwork, we take the security of our users very seriously. Upwork values the work done by security researchers in improving the security of our products and service offerings. We are committed to...

Bug Bounty Program / Reporting Security Issues
Building the world-class engineering team.

Create with Spring, sell on social - Spring. For creators.
Create and sell products to your fans with Spring. Creators can monetize their content and earn their fair share. Plus, it’s free.


Crypto Futures and Options Exchange - Deribit
World's biggest Bitcoin and Ethereum Options Exchange and the most advanced crypto derivatives trading platform with up to 50x leverage on Crypto Futures and Perps.

CargoCoin - Bounty Hunter & Affiliate Program
CargoCoin - Bounty Hunter & Affiliate Program

Mbed TLS
A C library implementing cryptographic primitives, X.509 certificate manipulation and the SSL/TLS and DTLS protocols.
TorGuard VPN’s Bug Bounty Program |

Security
Read our Security page to find out how we make sure that using the Transloadit service is as safe as it can be.

Privacy & Security | Trezor
Trezor is the safest crypto ecosystem-no personal data collected, seed generated & stored offline, full crypto custody.
Trustly
The TYPO3 Security Team

Security and Umbraco
Security is one of the main factors when creating digital projects. Discover how we make sure our product and services stay secure.

Unity QA: Building quality with passion
Unity QA provides building tools, frameworks and test suites for both end-users and corporate partners.
Your Cobrowsing Software Solution
Cobrowsing with Upscope: cobrowse customers’ screens live—no setup or downloads. Solve problems in seconds. Book your demo today
Your Cobrowsing Software Solution
Discover cobrowsing solutons with Upscope's cobrowsing software. Navigate websites with others in real-time for seamless teamwork and enhanced customer support.
Report a Bug - Blizzard Support
us.battle.net

Security on Vimeo
Join the web’s most supportive community of creators and get high-quality tools for hosting, sharing, and streaming videos in gorgeous HD with no ads.
CERT Coordination Center
The Vulnerability Notes Database provides information about software vulnerabilities.

Vulnerability Disclosure
Envato Product Security Security and privacy at Envato starts with our values. At Envato, we understand security and privacy is important because we are in it for the community. This means we’re committed to working with our community, including through our security program to recognize helpful...
 webuild.envato.com
webuild.envato.com

Responsible disclosure | WerkenbijDefensie.nl
Responsible disclosure Defensie wil zich inspannen voor optimale veiligheid en hecht grote waarde aan de security van haar eigen ICT-systemen. Toch valt noo...

WeTransfer is the simplest way to send your files around the world
WeTransfer is the simplest way to send your files around the world

Wickr | Bug Bounty Program
If you believe you have found security vulnerability in the Wickr Apps, we encourage you to report it to our Bug Bounty Program. Before you report a vulnerability, please review the program rules, including a responsible disclosure policy, rewards guidelines and the scope of the program.
 wickr.com
wickr.com

Report a security issue - 23andMe AU, DE, FR & EU
Submit any issues or vulnerabilities with the 23andMe website, product experience or applications.

Accenture Responsible Disclosure | Let there be change
Responsible Disclosure is a voluntary program through which Accenture will engage with parties who identify and report potential security vulnerabilities. Read more.
www.accenture.com
White Hat
Before reporting any security vulnerabilities to Accredible, please review the information on our Whitehat page including the process and exceptions sections.
Security – Actility | Global Leader in IoT connectivity solutions
Welcome to Actility Bug Bounty! Independent security researchers and our user community are welcome to help keeping Actility and its users secure.
Support and Training

Customer Service - Airbnb Help Center
Responsible Disclosure

Learn all about security & compliance at Algolia
Algolia’s search security team regularly tests for security issues and exploits. Algolia is SOC 2 & SOC 3 Compliant, ISO certified, and SAML SSO ready.


Page Not Found
404 Page not found! Sorry, but the page you were looking for could not be found. You can return to our homepage, or contact us if you can't find what

Security | Artsy
Artsy is the world’s largest online art marketplace. Browse over 1 million artworks by iconic and emerging artists from 4000+ galleries and top auction houses.


Responsible Disclosure Statement
BASF investigates all reports of security vulnerabilities affecting BASF web presence. If you are a security researcher and believe you have found a security vulnerability, please send an e-mail to us at [email protected].

Page Not Found

Vulnerability Security Testing & DAST | Beyond Security
Secure your applications and networks with the industry's only network vulnerability scanner to combine SAST, DAST and mobile security.
Trade forex, stocks, crypto, gold and commodities | Deriv
Award-winning online broker, rated excellent on Trustpilot. Sign up for a demo trading account to trade forex, stocks, and other financial markets.
Bug Bounty | Bitcoin.de
Bug Bounty
Whitehat bonus - bitcoinrekening


Responsible Disclosure Policy | HRMS - Human Capital Management - BizMerlinHR
Responsible Disclosure of Security Vulnerabilities
Blinksale | Easy Invoicing & Payments
Blinksale makes it easy to send invoices and track payments—so you can focus on doing more of the work that gets you paid.

The site is temporarily down

Box Vulnerability Reporting Policy
If you believe you've identified a potential security vulnerability, please report it to us right away. We will investigate all legitimate reports and do our best to quickly address the problems.
PayPal - Bug Bounty Program | HackerOne
The PayPal Bug Bounty Program enlists the help of the hacker community at HackerOne to make PayPal more secure. HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited.
www.braintreepayments.com
#1 Crowdsourced Cybersecurity Platform | Bugcrowd
Bugcrowd teams with elite security researchers to reduce risk & improve security ROI through our bug bounty, pen testing, & vulnerability disclosure programs.

Instructure | Bugcrowd
Learn why Instructure switched from traditional penetration testing to an on-demand bug bounty program for their Annual Security Audit.

Responsible Disclosure Policy
When vulnerabilities are found we’d like to learn of them as soon as possible, allowing us to take swift action to shore up our security.
The security of your data matters to us
The security of your data matters to us. Here's everything you need to know about the ways Campaign Monitor keeps maintains our security.
Security & Responsible Disclosure | Chalk
Chalk employs bank grade security and industry best practices to ensure that your data is safe and secure.
 www.chalk.com
www.chalk.com
JPMorgan Chase Responsible Disclosure Program
We want to hear from you if you have information related to potential security vulnerabilities of JPMorgan Chase products and services. We value your work and thank you in advance for your contribution.
Kwetsbaarheid melden | CJIB.nl
Waar kan ik melden dat ik een zwakke plek heb ontdekt in een ICT-systeem van het CJIB? Een zwakke plek in een ICT-systeem van de Rijksoverheid kunt u melden bij het Nationaal Cyber Security Centrum (NCSC). Het CJIB is onderdeel van de Rijksoverheid. Daarom kunt u een zwakke plek in een...

Vulnerability Disclosure Policy
This policy provides our guidelines for reporting vulnerabilities to Cloudflare.
Bug Bounty Program & Crypto Bounty Campaign
As part of our ongoing effort to keep your money safe and information secure, we run a bug bounty program. Visit CoinJar to learn more.
Thank you | Compose
craigslist | contact form error
www.craigslist.org
Error | Credit Karma
Instantly receive your free credit score and credit report card online. Free credit tools to track and optimize your credit score. No credit card needed & no hidden fees
www.creditkarma.com
Bug Bounty program

BlackBerry – Intelligent Security. Everywhere.
Based in Waterloo, Ontario, BlackBerry is a leader in secure communications — helping businesses, government agencies and safety-critical institutions of all sizes secure the Internet of Things (IoT).
Dash Bug Bounty Program
This thread is for updates and technical discussion of the Dash Bug Bounty Program. The Dash Bug Bounty Program is located here: https://bugcrowd.com/dashdigitalcash The Dash Bug Bounty Program is a DashIncubator project that is being managed by @jimbursch. Funding for the project was...

Security | Delivery Hero
Delivery Hero is the world's leading local delivery company. We are on a mission to deliver an amazing experience - fast, easy, and to your door.


DJI To Offer “Bug Bounty” Rewards For Reporting Software Issues - DJI
DJI, the world’s leader in civilian drones and aerial imaging technology, is establishing a “bug bounty” program to reward people who discover security issues with DJI software.

Secure Software Supply Chain - Docker
Docker offers secure software supply chain solutions for development teams. Build, share, and run secure applications without reducing productivity.
 www.docker.com
www.docker.com
Security | Doorkeeper

Security Response
Keeping our customers safe is a huge responsibility, and our highest priority. We pledge to deal with any security reports quickly, responsibly, and with the utmost care.

Security Vulnerability Disclosure Program
Also check out our EFF Security Hall of Fame to see the heroes that have already reported security vulnerabilities to us!OverviewEFF is committed to protecting the privacy and security of users of our software tools. Our Vulnerability Disclosure Program is intended to minimize the impact any...
EMP Trust HR Solution | Security Policy
EMPTRUST offer a Human Resource information solutions for a global workforce to meets new hire and employee onboarding efficiently.
www.emptrust.com

Report Security Vulnerabilities | ESET

Responsible Disclosure
At Erasmus University Rotterdam we work hard to maintain and improve the security of our systems; nevertheless vulnerabilities may occur in our systems. Our…

ExpressVPN’s Bug Bounty Program | ExpressVPN
Learn about ExpressVPN’s in-house bug-bounty program and how you can receive cash rewards for finding security flaws.

Vulnerability Reward Program
Discover WithSecure's™ vulnerability reward program. See the guide to reporting e-mail and server security issues, Linux security vulnerabilities, among others.
www.f-secure.com

Meta Bug Bounty
Meta Bug Bounty. Gefällt 363.808 Mal · 100 Personen sprechen darüber. Updates & announcements related to Meta Bug Bounty program. If you have found a security vulnerability, we encourage you to let...
 www.facebook.com
www.facebook.com

Security Issue Reporting
If you think you have found a security vulnerability in Fastmail, report it to us straight away. We promise to investigate all legitimate reports in a timely manner and fix any issues as soon as we can.

Firebase Support
Get help quickly with Firebase support. Read our FAQs, Release notes, and guides, ask the community, then get direct support from the Firebase team.

Report a Security Issue | FireEye
Have you discovered a potential cyber security issue? Visit FireEye and report it here.
FIRST bug bounty program

Security Contact | Foxy.io
We are intensely focused on keeping our customers’ data safe and secure here at Foxy. Any input that helps us better serve and protect our customers is welcome.

Responsible Disclosure of Security Vulnerabilities - FreshBooks
FreshBooks Responsible Disclosure policy outlines the guidelines for reporting any security vulnerabilities or concerns regarding our services.
Responsible disclosure GAMMA
GAMMA vindt de veiligheid en privacy van haar klanten erg belangrijk. Als je een zwakke plek in de beveiliging van één van onze systemen vindt, horen we dat graag.
Security and Privacy - Harvest

Android and Google Devices Security Reward Program Rules | Google Bug Hunters
The Android and Google Devices Security Reward program recognizes the contributions of security researchers who invest their time and effort in helping us secure our devices and platforms. Through this program, we provide monetary rewards and public...

Chrome Vulnerability Reward Program Rules | Google Bug Hunters
ATTENTION As of 4 February 2024, Chromium has migrated to a new issue tracker, please report security bugs to the new issue tracker using this form . Please see the Chrome VRP News and FAQ page for more updates and information. The Chrome...

Open Source Security Patch Rewards
The Patch Rewards program rewards proactive improvements to security in open source projects.

Google and Alphabet Vulnerability Reward Program (VRP) Rules | Google Bug Hunters
We have long enjoyed a close relationship with the security research community. To honor all the cutting-edge external contributions that help us keep our users safe, we maintain a Vulnerability Reward Program for Google-owned and Alphabet (Bet)...
Security at Tinder
With 43 billion matches to date, Tinder® is the world’s most popular dating app, making it the place to meet new people.
HackerEarth Bounty Program - program | HackerEarth
HackerEarth is a global hub of 5M+ developers. We help companies accurately assess, interview, and hire top developers for a myriad of roles.
 www.hackerearth.com
www.hackerearth.com

HackerRank
Join over 23 million developers in solving code challenges on HackerRank, one of the best ways to prepare for programming interviews.

Dropbox Security & Compliance Trust Center
The information and assurance you need to feel confident in beginning a more enlightened way of working with Dropbox.

Heroku Security | Heroku
Security Center | HID Global
Welcome to the HID Global Security Center. We take physical and digital security very seriously, with our experienced teams continuously working to strengthen security across our portfolio. To help

Bug Bounty & Vulnerability Research Program
Honeycomb encourages responsible disclosure of security vulnerabilities through our bug bounty program. Learn more about the basic features of our policy.

Hostinger Responsible Disclosure Policy and Bug Reward Program
Hostinger Responsible Disclosure Policy and Bug Reward Program are covered. Please, read it carefully and get familiar with this agreement.
Contribute to Coding – Hyperledger Foundation
Our projects are built by active community members – learn how to utilize and contribute to our development tools.

Responsible Disclosure of Security Vulnerabilities
We're working with the security community to make iFixit safe for everyone.
Responsible Disclosure Program
IKEA valora muchísimo la confianza que depositan los clientes. Por eso es tan importante la seguridad de nuestro sitio web. Si has descubierto vulnerabilidades en alguno de nuestros servicios, te agradeceríamos que nos informaras al respecto
Responsible Disclosure - Inflectra

ING.com security
ING provides the following general information to answer any concerns that you may have around the security of the internet, inclu
Trust Center
Intercom upholds the highest standards for safety and security, including enterprise-grade testing and controls, internationally recognized compliance accreditations, and advanced protections for Fin AI Agent against LLM threats.

Bug Bounty & Agile Pentesting Platform
Intigriti is Global bug bounty platform, vulnerability disclosure programs and penetration testing services provider.
Intrasurance overgenomen door Heinenoord Assuradeuren - Heinenoord Assuradeuren

MOVEit Secure Managed File Transfer Software | Progress
MOVEit is automated and secure Managed File Transfer software for sensitive data and advanced workflow automation capabilities without the need for scripting.

Bug Bounty - JetApps
Responsible Disclosure of Security Vulnerabilities We’re working with the security community to make our products safer for everyone! Security researchers play a vital role in safeguarding digital information. All vulnerability reports must adhere to our Bug Bounty Terms and Conditions. The...
 www.jetapps.com
www.jetapps.com

Report a Security Vulnerability | Juniper Networks US
Optimize security policies and thwart cyberattacks with adaptive threat intelligence integrated into your network. Please report any potential or real instances of security vulnerabilities with any Juniper Networks product to the Juniper Networks Security Incident Response Team.
www.juniper.net

Vulnerability Disclosure Policy
Vulnerability Disclosure Policy (“Policy”) outlines steps for reporting vulnerabilities to us, what we expect, and what you can expect from us.
KeepKey - Hardware Wallet | ShapeShift
Check out KeepKey - Hardware Wallet to help protect your cryptocurrencies and safeguard your assets from hackers.
 www.keepkey.com
www.keepkey.com

LiveAgent Bug Bounty Program | LiveAgent
Data security is one of our first priorities and we want to know about our blind spots. If you're a researcher we will appreciate and reward your help.

LiveAgent Bug Bounty program
Vulnerability disclosure program LiveAgent aims to keep its service safe for everyone, and data security is of utmost importance. Our Vulnerability
LähiTapiolan Bug Bounty -ohjelma täyttää vuoden – suurin palkinto nousee 50 000 euroon | LähiTapiola
LähiTapiolan Bug Bounty -ohjelma täyttää vuoden – suurin palkinto nousee 50 000 euroon

Transparent Security & Customer Data Protection - LastPass
LastPass pledges to protect our customers’ data, passwords, and vaults. We adhere to values of security, communication, and continuous improvements.

Bug Bounty Program
The whispers from the Donjon of Ledger. The latest news about security research at Ledger.
Security | Legal Robot
Know what you sign. Legal Robot uses machine learning to understand contracts. Snap a picture for instant analysis and write better contracts using AI.

Malwarebytes Bug Bounty and Vulnerability Disclosure Program
Malwarebytes welcomes and encourages independent researchers to report vulnerabilities in our products.
Drop Bounty
Join our community of passionate people to find and follow your interests in high quality mechanical keyboard & audiophile products. Discover innovative products, made possible by the collective wisdom of our users.

Security Vulnerability Report
If you believe you have discovered a security vulnerability in a Mattermost product, please fill out this form to report it.

Responsible Disclosure | Maximum
Optimizing safety when it comes to the ICT systems is a top priority for Maximum. However, as such systems remain vulnerable, possible loopholes and weakness...
Responsible Disclosure Policy
Mimecast understands that protecting customer data is paramount to your companies security. Learn more about it in our Responsible Disclosure Policy.

Mollie – Responsible disclosure
An advanced solution to accept payments, optimise conversion, and access funding.
 www.mollie.com
www.mollie.com

Security Bug Bounty Program
NDIX

NETGEAR Product Security | NETGEAR
Discover how we strive to earn and maintain the trust of our customers by delivering products that will protect the privacy and security of their data.
Nmbrs | Cloud HR and Payroll software
At Nmbrs, we regard the security of our platform, network and products, as the highest priority. Therefore we constantly monitor our business network.

Powering Digital Freedom for people
Gen is a global leader in cybersecurity. Explore our trusted brands including Norton, Avast, LifeLock, Avira, AVG, ReputationDefender, and CCleaner.
Press | Our Company | Yahoo Inc.
Verizon Media Platform blogs cover current product development news, platform information, and opinions on technology and issues impacting our industry.
Responsible Disclosure

Responsible Disclosure of Odoo Security Vulnerabilities
We want Odoo to be safe for everyone. If you've discovered a security vulnerability, please help us by reporting it in a responsible manner. Please find here our policy and our guidelines for reporting security issues.

OffSec's Bug Bounty Program | OffSec
Find out about OffSec's bug bounty program. We regularly conduct vulnerability research and are proponents of coordinated disclosure.
Olark: Security at Olark

OneLogin Compliance Commitment: Data & Privacy are #1
OneLogin is ISO 27001 Certified, issues SOC 1 and SOC 2 Type 2 reports, and meets U.S. Privacy Shield and GDPR requirements.
www.onelogin.com
https://www.open-xchange.com/resources/ox-blog/article/going-public-with-our-new-bug-bounty-program/
Vulnerabilities
If you think you have found a security bug in OpenSSL, please report it to us. Show issues fixed only in OpenSSL 3.3, 3.2, 3.1, 3.0, 1.1.1, 1.1.0, 1.0.2, 1.0.1, 1.0.0, 0.9.8, 0.9.7, 0.9.6 Note: All OpenSSL versions before 1.1.1 are out of support and no longer receiving updates. Extended support...
Vulnerability Policy
How Opera handles security threats, responsible disclosure, 0-day vulnerabilities, and more to keep users safe.

CERT Orange
C’est la structure opérationnelle chargée de gérer les incidents de sécurité informatique pouvant impacter les activités du Groupe, entités et filiales incluses.


- OVHcloud Blog
Accelerating with OVHcloud Engineering Partner Program Startup Program Product News Ecosystem Accelerating with OVHcloud Our latest updates on OVHcloud key business achievements, communities events and how we help our customers accelerate their transformation more… OVHcloud Engineering Follow...
 www.ovh.co.uk
www.ovh.co.uk

Responsible Disclosure
Through its SaaS-based platform, PagerDuty empowers developers, DevOps, IT operations and business leaders to prevent and resolve business-impacting
PayPal - Bug Bounty Program | HackerOne
The PayPal Bug Bounty Program enlists the help of the hacker community at HackerOne to make PayPal more secure. HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited.
www.paypal.com

Bug Bounty Program | Paysera
Notify us about a security breach or website vulnerabilities and receive a reward!

Philips Responsible Disclosure Statement | Philips
Philips is committed to ensuring the safety and security of patients, operators and customers who use our products and services.
POLi Payments | Australia’s leading real-time online debit payment system
POLi is Australia’s leading real-time online debit payment method. It offers a secure alternative to PayPal, BPAY and credit cards by giving customers the option to pay from their internet banking.

Responsible disclosure | Port of Rotterdam

Private Internet Access’ Vulnerability Disclosure Program
Learn how to participate in PIA VPN’s vulnerability disclosure program. Report bugs to improve the security of our products. Help us build a safer internet.

Welcome Aboard, Bug Bounty Hunters!
At Pushwoosh, we take the security of our users’ data very seriously. We introduce Bug Bounty program and encourage those bounty hunters who have discovered potential security vulnerabilities in Pushwoosh service to disclose it to us in a responsible manner. We will work with security...
Reporting a bug - QEMU

QIWI - Bug Bounty Program | HackerOne
The QIWI Bug Bounty Program enlists the help of the hacker community at HackerOne to make QIWI more secure. HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited.
www.qiwi.ru

Qualcomm Product Security | Qualcomm
Qualcomm Incorporated and its subsidiaries understand that maintaining a large variety of products comes with certain responsibilities. We take security vulnerabilities very seriously and always seek to respond appropriately.
White Hat Disclosure Policy | Rainforest QA
This page details our white hat disclosure policy, what we accept, how, as well as our hall of fame for accepted issues.


Razer Bug Bounty Program | Razer United States
Help us find bugs in our Synapse, Chroma, Cortex and other Razer software and stand to be rewarded.
Disclosure Policy | RCE Security
Responsible disclosure
The ICT systems of the Dutch Judiciary have to be safe. Contact point if you find vulnerabilities in the ICT-systems of the Judiciary.

Advanced Server Access | Okta
Okta Advanced Server Access provides a centralized control plane and zero trust server, allowing SSO extensions to your Linux and Windows servers via SSH & RDP.
www.scaleft.com
Data security, PCI compliance and fraud protection
Our online payment systems are PCI DSS compliant. Prevent fraudulent transactions with SecurePay's award winning fraud solution.
Report a Security Vulnerability
It is crucial that any potential security vulnerability is reported immediately to ensure they are resolved appropriately. Click here to contact us.

Privacy and Terms - Overleaf, Online LaTeX Editor
An online LaTeX editor that’s easy to use. No installation, real-time collaboration, version control, hundreds of LaTeX templates, and more.

Shopify Bug Bounty Program
We encourage security researchers to register for our bugbounty program.


Bug Bounty Program Launch | Silent Circle
Silent Circle launches its Bug Bounty Program, enabling the security researcher community to publicly submit and track security bugs.
Responsible disclosure
Simpplr aims to keep its Services safe for everyone, and data security is of utmost priority.

SiteGround Website Terms of Use
SiteGround Terms of Use. Find every detail about the legal agreement between you and SiteGround.com.

Security Standards | Slido - Audience Interaction Made Easy
We take security of your data very seriously. Read more about how we handle your data and the security standards we have in Slido.

Responsible Disclosure Policy for Security Vulnerabilities
Smokescreen works closely with security researchers to identify and fix any security vulnerabilities in our infrastructure and products. If you believe you have found a security issue, we encourage you to notify us and work with us on the lines of this disclosure policy.
Bounty - Solar Accounts

Secure Managed Cloud - Solvinity
Een betrouwbare, veilige IT-omgeving nodig? Solvinity ondersteunt je met Secure Managed Cloud services. Lees alles over onze services en organsiatie.

Cybersecurity as a Service Delivered | Sophos
We Deliver Superior Cybersecurity Outcomes for Real-World Organizations Worldwide with a Broad Portfolio of Advanced Security Products and Services.

Spokeo | People Search | Security
People search engine and free white pages finds phone, address, email, and photos. Find people by name, email, address, and phone for free.
Zip Business Capital | Small business loans
Need funds to grow your business? Get an unsecured line of credit of up to $500,000. Decisions within 24 hours and terms up to 5 years.


Bug Bounty Program | Spreaker Help Center

Security & Compliance at Sqreen | Sqreen
Keeping our customers' data safe is our priority. Learn what security best practices we follow to protect our customers.
Starbucks - Bug Bounty Program | HackerOne
The Starbucks Bug Bounty Program enlists the help of the hacker community at HackerOne to make Starbucks more secure. HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited.
www.starbucks.com

StarLeaf - Secure, reliable, intuitively simple enterprise video meetings
StarLeaf brings people together to work better, with enterprise-grade video meetings that are secure, reliable and intuitively simple.

Stellar | Bug Bounty Program
The Stellar Bug Bounty Program provides bounties for vulnerabilities and exploits discovered in the Stellar protocol or any of the code in our repos.
 www.stellar.org
www.stellar.org
Bug Bounty: closes security gaps | Swisscom
Our Bug Bounty programme supports the reporting and elimination of security gaps and weak points in our products and services.

Blockchain, Bug Bounties and Björk
Two days ago, the US Securities and Exchange Commission clarified their position on cryptocurrencies, a hot topic in the investment world. It is also one that seems to get more heated with each rise and fall in their value. In the SEC’s announcement, they mandated that all coin exchanges must...
www.synack.com

Security Bug Bounty Program | Synology Inc.
We operate the Security Bounty Program to give recognition and monetary rewards to researchers that have identified potential vulnerabilities of our products.
Responsible Vulnerability Disclosure Best Practices | Black Duck Blog
Explore best practices for responsible vulnerability disclosure to mitigate risks and prevent malicious use of technical weaknesses in software security.

GDPR
Talent LMS cares about its users’ data confidentiality, integrity, privacy and availability. Read about the ways we protect the data gathered by our learning management system. If in doubt, contact us.

Closing security gaps
Deutsche Telekom is starting its own Bug Bounty program to make its products more secure.

Product Security | Tesla
Tesla is committed to working with the community to verify, reproduce and respond to legitimate reported product vulnerabilities. Learn more about Tesla's product security policy and responsible disclosure guidelines.

Quality Assurance
Quality Assurance - powered by crowdtesting and device cloud: Challenge bugs and performance issues with Testbirds QA services

Responsible Disclosure of Security Vulnerabilities
The Atlantic covers news, politics, culture, technology, health, and more, through its articles, podcasts, videos, and flagship magazine.

Traveloka Bug Bounty Program
Traveloka is committed to keep its services safe for everyone, which is why data security is our utmost priority. Traveloka welcomes any contributions and information by security researchers who find various types of security vulnerabilities seen in our services, in which case we would be...
www.traveloka.com

Accept card payments safely and easily worldwide | TrustPay
Receive payments from millions of Visa and MasterCards holders worldwide and accept payments safely and easily in 170+ currencies.
Reporting Security Vulnerabilities | Twilio
www.twilio.com

Welcome All Bug Bounty Hunters
Today we’re excited to announce our official bug bounty program and a first of its kind loyalty reward program for bounty hunters. Learn more now.

Ubiquiti - Rethinking IT
Technology platforms for Internet Access, Enterprise, and SmartHome applications.

Security
For Unitag, security is a priority. Help us make the platform an increasingly safe place.
Private banking
Persoonlijk, deskundig en resultaatgericht. Uw wensen en doelen staan centraal en u krijgt deskundig advies op maat.
Report Security Vulnerability | Verizon Wireless
See a security vulnerability? Say something. Tell Verizon more about your issues with phones, internet, business services or anything else so we can help!
www.verizonwireless.com

Security

Cyber Security | Vodafone
Die Sicherheit unserer Netze, Systeme und Kund:innen hat höchste Priorität - und ist ein grundlegender Bestandteil unseres Unternehmenszwecks. Alles zu Cyber Security bei Vodafone findest Du auf dieser Seite.
Security and Operations Control Center - Vrije Universiteit Amsterdam
SOCC investigates and coordinates matters pertaining to information security incidents involving staff, students and/or systems at VU Amsterdam.
WhatRuns - Discover Website Technologies | Identify CMS, Frameworks, and More
WhatRuns - Discover what runs a website
Xen Security Problem Response Process - Xen Project
This document has come in effect in December 2011 and will be reviewed periodically: see Change History for a detailed list of changes. Introduction Computer systems have bugs. Currently recognised...
www.xenproject.org

Zynga’s Responsible Disclosure Program - Zynga
Zynga is dedicated to providing a safe and fair gaming environment for our players. If you believe you’ve found a security vulnerability or game logic bug (each, a “Vulnerability”) in our applications or services (our “Services”) that could adversely affect Zynga or our players, or give an...
 www.zynga.com
www.zynga.com

Security Exploit Bounty Program
Closure of Public Bounty ProgramAs of 20 January 2022 we have closed our public bounty program in favour of a managed program through HackerOne. While our HackerOne program is not currently public, we still welcome submissions from security researchers! Please use the form linked below to...
Home | Firo - Privacy-preserving cryptocurrency
Firo is a digital currency with a focus on setting privacy standards.
Contact Us | ZenMate VPN | Security made simple
Having trouble or have a question? Reach out and contact us!







